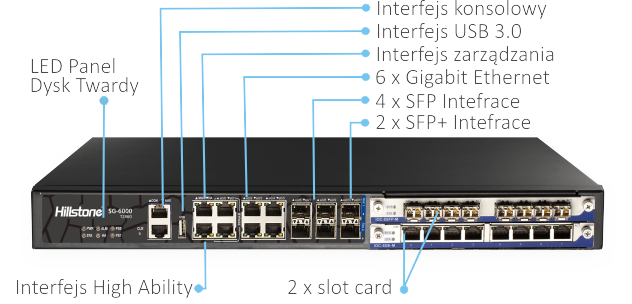
Hillstone Networks Seria-T
Pierwsza inteligentna zapora ogniowa (iNGFW) i jednocześnie pierwszy firewall czwartej generacji. Jest w stanie wykrywać nieznane złośliwe oprogramowanie i podejrzane nieprawidłowe zachowanie obiektów w sieci. Obsługuje głęboką kontrolę pakietów (DPI), zaawansowaną kontrolę aplikacji, czy jakość usług (QoS). Jest również ekologiczny – zachowując wysoką wydajność, cechuje go niskie zużycie energii.
Uczenie maszynowe i sztuczna inteligencja
Seria T Hillstone iNGF wykorzystuje trzy kluczowe technologie do wykrywania zaawansowanych ataków i ciągłej ochrony sieci przed zagrożeniami:
1. Klastry statystyczne wykorzystujące autorski silnik Hillstone NetworksAdvanced Threat Detection wykrywa 0-day (Hillstone ATD).
2. Po przez analitykę behawioralną w czasie rzeczywistym tworzy model matematyczny użytkownika, wykrywającą anomalii w zachowaniu sieci, opartą o technologię Hillstone Abnormal Behavior Detection (Hillstone ABD).
3. Silnik analizy korelacji zagrożeń (Hillstone ATC), który wykorzystuje do tego dane zebrane przez pozostałe technologie: ATD, ABD, sandbox, sygnatury, itd. – wraz z informacjami kontekstowymi w celu identyfikacji zaawansowanych zagrożeń.
Specyfikacje modeli:
Modele urządzeń serii T
Hillstone iNGFW T-1860

Sztuczna Inteligencja+ML
Przepustowość Firewall – 8 Gbps

Przepustowość IPSec – 3 Gbps

Przepustowość Antywirusa – 1.6 Gbps

Przepustowość IPS – 3 Gbps

Przepustowość NGFW* – 1 Gbps

Maksymalna ilość sesji – 1 500 000

Hillstone iNGFW T-2860

Sztuczna Inteligencja+ML
Przepustowość Firewall – 10 Gbps

Przepustowość IPSec – 3.8 Gbps

Przepustowość Antywirusa – 2 Gbps

Przepustowość IPS – 4 Gbps

Przepustowość NGFW* – 1.5 Gbps

Maksymalna ilość sesji – 3 000 000

Korelacja i analiza zagrożeń
Dzięki Hillstone ATC możliwa jest dokładna analiza z wykorzystaniem informacji z pozostałych modułów. Każde wykryte w ten sposób zagrożenie ze strony złośliwego kodu, jest automatycznie łączone z krokami w tzw. „Kill Chain”. Dzięki obszernym danym, uzupełniony zostaje on o bogaty kontekst dla analityków bezpieczeństwa w firmie – np. ustalenie źródła ataku, jego siły i zastosowanej metodologii. Ponadto Hillstone zapewnia również opcję przechwytywania pakietów, co w połączeniem z syslogiem i dziennikami ruchu, zapewniają szereg dodatkowych informacji, również w celach dochodzeniowych i kryminalistycznych.
Urządzenie które samo się uczy
Silnik Hillstone Abnormal Behavior stale uczy się sieci, aby dowiedzieć się, jak wygląda normalny ruch sieciowy dla danego dnia i czasu. Alertuje na podstawie zbadanego ruchu, gdy aktywność sieciowa przekracza obliczone progi. Używa do tego celu ponad 50 tablic wymiarowych, które służą do kalkulowania normalnego ruchu sieciowego w warstwach L4-L7. Proces ten określany jest jako “modelowanie zachowania”. Dodatkowo został on przeszkolony prawdziwymi narzędziami hakerskimi w celu zapewnienia, że szkodliwe działania będą prawidłowo rozpoznawane. Techniki te ograniczają liczbę false positive i zapewniają użytkownikowi wiele możliwości zatrzymania ataku.
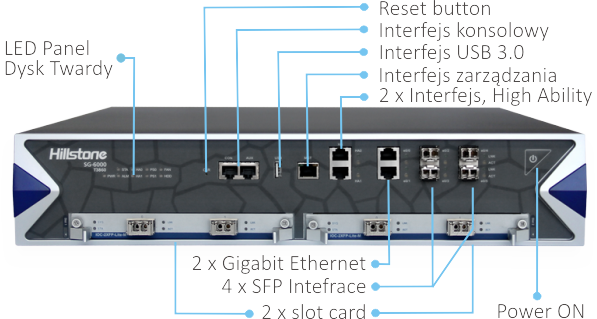
Hillstone iNGFW T-3860

Sztuczna Inteligencja+ML
Przepustowość Firewall – 20 Gbps

Przepustowość IPSec – 12 Gbps

Przepustowość Antywirusa – 6 Gbps

Przepustowość IPS – 8 Gbps

Przepustowość NGFW* – 5 Gbps

Maksymalna ilość sesji – 4 000 000

Hillstone iNGFW T-5060

Sztuczna Inteligencja+ML
Przepustowość Firewall – 25 Gbps

Przepustowość IPSec – 15 Gbps

Przepustowość Antywirusa – 7 Gbps

Przepustowość IPS – 12 Gbps

Przepustowość NGFW* – 8 Gbps

Maksymalna ilość sesji – 5 000 000

Hillstone iNGFW T-5860

Sztuczna Inteligencja+ML
Przepustowość Firewall – 40 Gbps

Przepustowość IPSec – 28 Gbps

Przepustowość Antywirusa – 10 Gbps

Przepustowość IPS – 18 Gbps

Przepustowość NGFW* – 12 Gbps

Maksymalna ilość sesji – 6 000 000

Systemy ochrony i usługi
Threat Correlation Analytics
- Correlation among unknown threats, abnormal behavior and application behavior to discover potential threat or attacks
- Multi-dimension correlation rules, automatic daily update from the cloud
Advanced Threat Detection
- Behavior-based advanced malware detection
- Detection of more than 2000 known and unknown malware families including Virus, Worm, Trojan, Overflow etc.
- Real-time, online, malware behavior model database update
Abnormal Behavior Detect
- Behavior modeling based on L3-L7 baseline traffic to reveal anomalous network behavior, such as HTTP scanning, Spider, SPAM, SSH/FTP weak password
- Detection of DDoS including Flood, Sockstress, zip of death, reflect, DNS query, SSL DDos and application DDoS
Supports inspection of encrypted tunneling traffic for unknown applications - Real-time, online, abnormal behavior model database update
Threat Visibility and Mitigation
- Network risk index, critical assets and host risk status, host and threat risk severity and certainty
- Kill chain mapping of threat events on each host
- Threat forensic including threat analysis, knowledge base, history and PCAP.
- Predefined and customized mitigation rules
- Support threat whitelist
Network services
- Dynamic routing (OSPF, BGP, RIPv2)
- Static and policy routing
- Route controlled by application
- Built-in DHCP, NTP, DNS server and DNS proxy
- Tap mode—connect to SPAN port
Interface modes: sniffer, port aggregated, loopback, VLANS (802.1Q and trunking) - L2/L3 switching & routing
- Virtual wire (Layer 1) transparent inline deployment
Firewall
- Operating modes: NAT/route, transparent (bridge), and mixed mode
- Policy objects: predefined, custom, and object grouping
- Security policy based on application, role and geo-location
- Application Level Gateways and session support: MSRCP, PPTP, RAS, RSH, SIP, FTP, TFTP, HTTP, dcerpc, dns-tcp, dns-udp, H.245 0, H.245 1, H.323
- NAT and ALG support: NAT46, NAT64, NAT444, SNAT, DNAT, PAT, Full Cone NAT, STUN
- NAT configuration: per policy and central NAT table
- VoIP: SIP/H.323/SCCP NAT traversal, RTP pin holing
- Global policy management view
- Security policy redundancy inspection, policy group, policy configuration rollback
- Policy Assistant for easy detailed policy deployment
- Policy analyzing and invalid policy cleanup
- Comprehensive DNS policy
- Schedules: one-time and recurring
Intrusion Prevention
- Protocol anomaly detection, rate-based detection, custom signatures, manual, automatic push or pull signature updates, integrated threat encyclopedia
- IPS Actions: default, monitor, block, reset (attackers IP or victim IP, incoming interface) with expiry time
- Packet logging option
- Filter Based Selection: severity, target, OS, application or protocol
- IP exemption from specific IPS signatures
- IDS sniffer mode
- IPv4 and IPv6 rate based DoS protection with threshold settings against TCP Syn flood, TCP/UDP/SCTP port scan, ICMP sweep, TCP/UDP/SCIP/ICMP session flooding (source/destination)
- Active bypass with bypass interfaces
- Predefined prevention configuration
Anti-Virus
- Manual, automatic push or pull signature updates
- Flow-based Antivirus: protocols include HTTP, SMTP, POP3, IMAP, FTP/SFTP
- Compressed file virus scanning
Attack Defense
- Abnormal protocol attack defense
- Anti-DoS/DDoS, including SYN Flood, DNS Query Flood defense
- ARP attack defense
URL Filtering
- Flow-based web filtering inspection
- Manually defined web filtering based on URL, web content and MIME header
- Dynamic web filtering with cloud-based real-time categorization database: over 140 million URLs with 64 categories (8 of which are security related)
- Web filtering profile override: allows administrator to temporarily assign different profiles to user/group/IPAdditional web filtering features:
- Filter Java Applet, ActiveX and/or cookie
- Block HTTP Post
- Log search keywords
- Exempt scanning encrypted connections on certain categories for privacy
- Web filter local categories and category rating override
Anti-Spam
- Real-time Spam Classification and Prevention
- Confirmed Spam, Suspected Spam, Bulk Spam, Valid Bulk
- Protection Regardless of the language, format, or content of the message
- Support both SMTP and POP3 email protocols
- Inbound and outbound detection
- White lists to allow emails from trusted domains
Cloud-Sandbox
- Upload malicious files to cloud sandbox for analysis
- Support protocols including HTTP/HTTPS, POP3, IMAP, SMTP and FTP
- Support file types including PE,ZIP, RAR, Office, PDF, APK, JAR and SWF
- File transfer direction and file size control
- Provide complete behavior analysis report for malicious files
- Global threat intelligence sharing, real-time threat blocking
- Support detection only mode without uploading files
Botnet C&C Prevention
- Discover intranet botnet host by monitoring C&C connections and block further advanced threats such as botnet and ransomware
- Regularly update the botnet server addresses
- prevention for C&C IP and domain
- Support TCP, HTTP, and DNS traffic detection
- IP and domain whitelists
IP Reputation
- Identify and filter traffic from risky IPs such as botnet hosts, spammers, Tor nodes, breached hosts, and brute force attacks
- Logging, dropping packets, or blocking for different types of risky IP traffic
- Regular IP reputation signature database upgrade
SSL Decryption
- Application identification for SSL encrypted traffic
- IPS enablement for SSL encrypted traffic
- AV enablement for SSL encrypted traffic
- URL filter for SSL encrypted traffic
- SSL Encrypted traffic whitelist
- SSL proxy offload mode
Endpoint Identification and Control
- Support to identify endpoint IP, endpoint quantity, on-line time, off-line time, and on-line duration
- Support 10 operation systems including Windows, iOS, Android, etc.
- Support query based on IP, endpoint quantity, control policy and status etc.
- Support the identification of accessed endpoints quantity across layer 3, logging and interference on overrun IP
- Redirect page display after custom interference operation
- Supports blocking operations on overrun IP
Data Security
- File transfer control based on file type, size and name
- File protocol identification, including HTTP, FTP, SMTP and POP3
- File signature and suffix identification for over 100 file types
- Content filtering for HTTP-GET, HTTP-POST, FTP and SMTP protocols
- IM identification and network behavior audit
- Filter files transmitted by HTTPS using SSL Proxy
Application control
- Over 3,000 applications that can be filtered by name, category, subcategory, technology and risk
- Each application contains a description, risk factors, dependencies, typical ports used, and URLs for additional reference
- Actions: block, reset session, monitor, traffic shaping
- Identify and control applications in the cloud
- Provide multi-dimensional monitoring and statistics for applications running in the cloud, including risk category and characteristics
Quality of Service (QoS)
- Max/guaranteed bandwidth tunnels or IP/user basis
- Tunnel allocation based on security domain, interface, address, user/user group, server/server group, application/app group, TOS, VLAN
- Bandwidth allocated by time, priority, or equal bandwidth sharing
- Type of Service (TOS) and Differentiated Services (DiffServ) support
- Prioritized allocation of remaining bandwidth
- Maximum concurrent connections per IP
- Bandwidth allocation based on URL category
- Bandwidth limit by delaying access for user or IP
- Automatic expiration cleanup and manual cleanup of user used traffic
Server Load balancing
- Weighted hashing, weighted least-connection, and weighted round-robin
- Session protection, session persistence and session status monitoring
- Server health check, session monitoring and session protection
VPN
- IPSec VPN:
- IPSEC Phase 1 mode: aggressive and main ID protection mode
- Peer acceptance options: any ID, specific ID, ID in dialup user group
- Supports IKEv1 and IKEv2 (RFC 4306)
- Authentication method: certificate and pre-shared key
- IKE mode configuration support (as server or client)
- DHCP over IPSEC
- Configurable IKE encryption key expiry, NAT traversal keep alive frequency
- Phase 1/Phase 2 Proposal encryption: DES, 3DES, AES128, AES192, AES256
- Phase 1/Phase 2 Proposal authentication: MD5, SHA1, SHA256, SHA384, SHA512
- Phase 1/Phase 2 Diffie-Hellman support: 1,2,5
- XAuth as server mode and for dialup users
- Dead peer detection
- Replay detection
- Autokey keep-alive for Phase 2 SA
- SSL VPN realm support: allows multiple custom SSL VPN logins associated with user groups (URL paths, design)
- IPSEC VPN configuration options: route-based or policy based
- IPSEC VPN deployment modes: gateway-to-gateway, full mesh, hub-and-spoke, redundant tunnel, VPN termination in transparent mode
- One time login prevents concurrent logins with the same username
- SSL portal concurrent users limiting
- SSL VPN port forwarding module encrypts client data and sends the data to the application server
- Supports clients that run iOS,Android,and Windows XP/Vista including 64-bit Windows OS
- Host integrity checking and OS checking prior to SSL tunnel connections
- MAC host check per portal
- Cache cleaning option prior to ending SSL VPN session
- L2TP client and server mode, L2TP over IPSEC, and GRE over IPSEC
- View and manage IPSEC and SSL VPN connections
- PnPVPN
IPv6
- Management over IPv6, IPv6 logging and HA
- IPv6 tunneling, DNS64/NAT64 etc.
- IPv6 routing including static routing, policy routing, ISIS, RIPng, OSPFv3 and BGP4+
- IPS, Application identification, URL filtering, Anti-Virus, Access control, ND attack defense
- Track address detection
VSYS
- System resource allocation to each VSYS
- CPU virtualization
- Non-root VSYS support firewall, IPSec VPN, SSL VPN, IPS, URL filtering
- VSYS monitoring and statistic
High availability
- Redundant heartbeat interfaces
- Active/Active and Active/Passive
- Standalone session synchronization
- HA reserved management interface
- Failover:
- Port, local & remote link monitoring
- Stateful failover
- Sub-second failover
- Failure notification
- Deployment options:
- HA with link aggregation
- Full mesh HA
- Geographically dispersed HA
User and Device Identity
- Local user database
- Remote user authentication: TACACS+, LDAP, Radius, Active
- Single-sign-on: Windows AD
- 2-factor authentication: 3rd party support, integrated token server with physical and SMS
- User and device-based policies
- User group synchronization based on AD and LDAP
- Support for 802.1X, SSO Proxy
- WebAuth page customization
- Interface based Authentication
- Agentless ADSSO (AD Polling)
- Use authentication synchronization based on SSO-monitor
- Support MAC-based user authentication
Administration
- Management access: HTTP/HTTPS, SSH, telnet, console
- Central management: Hillstone Security Manager (HSM), web service APIs
- System integration: SNMP, syslog, alliance partnerships
- Rapid deployment: USB auto-install, local and remote script execution
- Dynamic real-time dashboard status and drill-in monitoring widgets
- Language support: English
Logs & reporting
- Logging facilities: local memory and storage (if available), multiple syslog servers and multiple Hillstone Security Audit (HSA) platforms
- Encrypted logging and log integrity with HSA scheduled batch log uploading
- Reliable logging using TCP option (RFC 3195)
- Detailed traffic logs: forwarded, violated sessions, local traffic, invalid packets
- Comprehensive event logs: system and administrative activity audits, routing & networking, VPN, user authentications, WiFi related events
- IP and service port name resolution option
- Brief traffic log format option
- Three predefined reports: Security, Flow and network reports
- User defined reporting
- Reports can be exported in PDF, Word and HTML via Email and FTP
Statistics and Monitoring
- Application, URL, threat events statistic and monitoring
- Real-time traffic statistic and analytics
- System information such as concurrent session, CPU, Memory and temperature
- iQOS traffic statistic and monitoring, link status monitoring
- Support traffic information collection and forwarding via Netflow (v9.0)