Urządzenie IPS działające w linii z prędkością drutu
Ponieważ krajobraz zagrożeń ewoluuje agresywnie, szybko pojawiła się rosnąca liczba technologii ochrony sieci. Spośród tych różnych technologii system zapobiegania włamaniom (IPS) pozostaje jednym z najczęściej wdrażanych rozwiązań, niezależnie od platformy i formy.
Urządzenie IPS (NIPS) firmy Hillstone Network działa w trybie ciągłym i przewodowym, wykonując głęboką kontrolę pakietów i kontrolę całego ruchu sieciowego. Stosuje również reguły oparte na kilku metodach, w tym analizie anomalii protokołu i analizie sygnatur w celu blokowania zagrożeń. Hillstone NIPS może zostać wdrożony w sieci w celu kontroli ruchu pozostawionego niezauważonym przez rozwiązania obwodowe i jest integralną częścią systemów bezpieczeństwa sieci ze względu na jego wysoką wydajność, bezkompromisowość, najlepsze w swojej klasie możliwości ochrony oraz szerokie i elastyczne scenariusze wdrażania.
Hillstone Networks Seria-S NIPS
Seria Hillstone S odgrywa integralną część systemów bezpieczeństwa sieci ze względu na jego wysoką wydajność. Dzięki systemowi NIPS uzyskasz dodatkową warstwę ochrony antywłamaniowa i antywirusową wewnątrz sieci. NIPS to brak kompromisów, najlepsze w swojej klasie możliwości ochrony oraz szerokie i elastyczne scenariusze wdrażania.
Specyfikacje modeli:

Specyfikacje urządzeń NIPS
Hillstone NIPS S600

Intrusion Prevention System
Stoneshield
—– brak —–
IPS throughput – 1Gbps

New connections per second 9 000

Maximum Connections (TCP) 600 000

Latency <100 μs

Hillstone NIPS S1060

Intrusion Prevention System
Stoneshield
—– brak —–
IPS throughput – 3Gbps

New connections per second 35 000

Maximum Connections (TCP) 1 000 000

Latency <100 μs

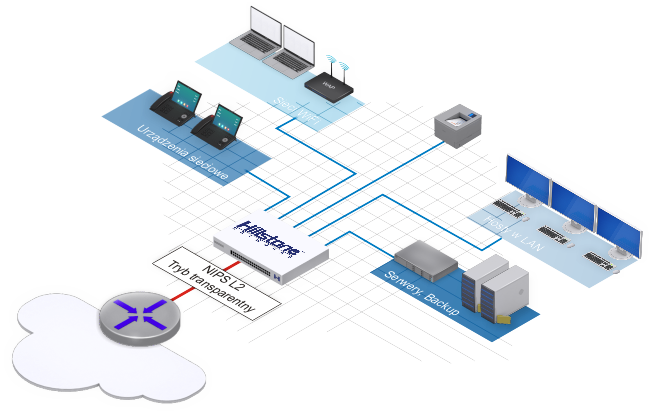
Ochrona przed zagrożeniami bez opóźnień
Platforma Hillstone NIPS ma najbardziej wszechstronny silnik inspekcji o wysokiej wydajności w połączeniu z najlepszym w swojej klasie podpisem partnerów z wiodącymi partnerami technologicznymi, zapewniając klientom najwyższy wskaźnik wykrywania zagrożeń przy najniższym całkowitym koszcie posiadania (TCO). Ponadto zapewnia wysoką przepustowość, małe opóźnienia i maksymalną dostępność w celu utrzymania wydajnych operacji bezpieczeństwa bez obniżania wydajności sieci.
Hillstone NIPS S1200

Intrusion Prevention System
Stoneshield

IPS throughput – 3Gbps

New connections per second 40 000

Maximum Connections (TCP) 1 200 000

Latency <300 μs

Hillstone NIPS S1560

Intrusion Prevention System
Stoneshield

IPS throughput – 4Gbps

New connections per second 32 000

Maximum Connections (TCP) 2 000 000

Latency <100 μs

Hillstone NIPS S1900

Intrusion Prevention System
Stoneshield

IPS throughput – 3,8Gbps

New connections per second 49 000

Maximum Connections (TCP) 1 200 000

Latency <70 μs

Hillstone NIPS S2100

Intrusion Prevention System
Stoneshield

IPS throughput – 5Gbps

New connections per second 150 000

Maximum Connections (TCP) 4 000 000

Latency <100 μs

Hillstone NIPS S2300

Intrusion Prevention System
Stoneshield

IPS throughput – 9Gbps

New connections per second 61 000

Maximum Connections (TCP) 3 000 000

Latency <300 μs

Hillstone NIPS S2700

Intrusion Prevention System
Stoneshield

IPS throughput – 12Gbps

New connections per second 65 000

Maximum Connections (TCP) 6 000 000

Latency <100 μs

Hillstone NIPS S3500

Intrusion Prevention System
Stoneshield

IPS throughput – 17Gbps

New connections per second 135 000

Maximum Connections (TCP) 8 000 000

Latency <300 μs

Hillstone NIPS S3900

Intrusion Prevention System
Stoneshield

IPS throughput – 25Gbps

New connections per second 320 000

Maximum Connections (TCP) 12 000 000

Latency <300 μs

Hillstone NIPS S5500

Intrusion Prevention System
Stoneshield

IPS throughput – 45Gbps

New connections per second 652 000

Maximum Connections (TCP) 24 000 000

Latency <100 μs

Hillstone NIPS S5560

Intrusion Prevention System
Stoneshield

IPS throughput – 50Gbps

New connections per second 485 000

Maximum Connections (TCP) 8 000 000

Latency <100 μs

Zamów dialog techniczny, porozmawiamy o zaletach rozwiązania
oraz pokaże Ci w praktyce jak działa NIPS Hillstone Networks
tel.531 464 002 email: mateusz.g@zabezpieczenia.it

Systemy ochrony i usługi
Intrusion Prevention
- 8,000+ signatures, protocol anomaly detection, rate-based detection, custom signatures, manual, automatic push or pull signature updates, integrated threat encyclopedia
- IPS actions: default, monitor, block, reset (attackers IP or attackers IP and victim IP, incoming interface) with expiry time
- Packet logging option
- Filter based selection: severity, target, OS, application and/or protocol
- IP exemption from specific IPS signatures
- IDS sniffer mode
- IPv4 and IPv6 rate based DOS protection with threshold settings against TCP Syn flood, TCP/UDP/SCTP port scan, ICMP sweep, TCP/UDP/SCIP/ICMP session flooding (source/destination)
- Active bypass with bypass interfaces
- Predefined prevention configuration
Threat Correlation Analytics
- Correlation among unknown threats, abnormal behavior and application behavior to discover potential threat or attacks
- Multi-dimension correlation rules, automatic daily update from the cloud
Advanced Threat Detection
- Behavior-based advanced malware detection
- Detection of more than 2000 known and unknown malware families including Virus, Worm, Trojan, Overflow etc.
- Real-time, online, malware behavior model database update
Abnormal Behavior Detect
- Behavior modeling based on L3-L7 baseline traffic to reveal anomalous network behavior, such as HTTP scanning, Spider, SPAM, SSH/FTP weak password
- Detection of DDoS including Flood, Sockstress, zip of death, reflect, DNS query, SSL DDos and application DDoS
Supports inspection of encrypted tunneling traffic for unknown applications - Real-time, online, abnormal behavior model database update
Antivirus
- Over 13 million AV signatures
- Flow-based Antivirus: protocols include HTTP, SMTP, POP3, IMAP, FTP/SFTP
- Supports compressed file virus scanning
Attack Defense
- Abnormal protocol attack defense
- Anti-DoS/DDoS, including SYN Flood, DNS Query Flood defense
- ARP attack defense
URL Filtering
- Flow-based web filtering inspection
- Manually defined web filtering based on URL, web content and MIME header
- Dynamic web filtering with cloud-based real-time categorization database: over 140 million URLs with 64 categories (8 of which are security related)
- Web filtering profile override: allows administrator to temporarily assign different profiles to user/group/IPAdditional web filtering features:
- Filter Java Applet, ActiveX and/or cookie
- Block HTTP Post
- Log search keywords
- Exempt scanning encrypted connections on certain categories for privacy
- Web filter local categories and category rating override
Anti-Spam
- Real-time Spam Classification and Prevention
- Confirmed Spam, Suspected Spam, Bulk Spam, Valid Bulk
- Protection Regardless of the language, format, or content of the message
- Support both SMTP and POP3 email protocols
- Inbound and outbound detection
- White lists to allow emails from trusted domains
Cloud-Sandbox
- Upload malicious files to cloud sandbox for analysis
- Support protocols including HTTP/HTTPS, POP3, IMAP, SMTP and FTP
- Support file types including PE,ZIP, RAR, Office, PDF, APK, JAR and SWF
- File transfer direction and file size control
- Provide complete behavior analysis report for malicious files
- Global threat intelligence sharing, real-time threat blocking
- Support detection only mode without uploading files
Botnet C&C Prevention
- Discover intranet botnet host by monitoring C&C connections and block further advanced threats such as botnet and ransomware
- Regularly update the botnet server addresses
- prevention for C&C IP and domain
- Support TCP, HTTP, and DNS traffic detection
- IP and domain whitelists
IP Reputation
- Identify and filter traffic from risky IPs such as botnet hosts, spammers, Tor nodes, breached hosts, and brute force attacks
- Logging, dropping packets, or blocking for different types of risky IP traffic
- Regular IP reputation signature database upgrade
Application control
- Over 3,000 applications that can be filtered by name, category, subcategory, technology and risk
- Each application contains a description, risk factors, dependencies, typical ports used, and URLs for additional reference
- Actions: block, reset session, monitor, traffic shaping
- Identify and control applications in the cloud
- Provide multi-dimensional monitoring and statistics for applications running in the cloud, including risk category and characteristics
Quality of Service (QoS)
- Max/guaranteed bandwidth tunnels or IP/user basis
- Tunnel allocation based on security domain, interface, address, user/user group, server/server group, application/app group, TOS, VLAN
- Bandwidth allocated by time, priority, or equal bandwidth sharing
- Type of Service (TOS) and Differentiated Services (DiffServ) support
- Prioritized allocation of remaining bandwidth
- Maximum concurrent connections per IP
- Bandwidth allocation based on URL category
- Bandwidth limit by delaying access for user or IP
- Automatic expiration cleanup and manual cleanup of user used traffic
IPv6
- Management over IPv6, IPv6 logging and HA
- IPv6 tunneling, DNS64/NAT64 etc.
- IPv6 routing including static routing, policy routing, ISIS, RIPng, OSPFv3 and BGP4+
- IPS, Application identification, URL filtering, Anti-Virus, Access control, ND attack defense
- Track address detection
VSYS
- System resource allocation to each VSYS
- CPU virtualization
- Non-root VSYS support firewall, IPSec VPN, SSL VPN, IPS, URL filtering
- VSYS monitoring and statistic
High availability
- Redundant heartbeat interfaces
- Active/Active and Active/Passive
- Standalone session synchronization
- HA reserved management interface
- Failover:
- Port, local & remote link monitoring
- Stateful failover
- Sub-second failover
- Failure notification
- Deployment options:
- HA with link aggregation
- Full mesh HA
- Geographically dispersed HA
Visible Administration
- Management access: HTTP/HTTPS, SSH, telnet, console
- Central Management: Hillstone Security Manager (HSM), web service APIs
- Two-factor authentication: username/password, HTTPS certificates file
- System Integration: SNMP, syslog, alliance partnerships
- Rapid deployment: USB auto-install, local and remote script execution
- Dynamic real-time dashboard status and drill-in monitoring widgets
- Storage device management: storage space threshold customization and alarm, old data overlay, stop recording.
- Language support: English
Logs & reporting
- Logging facilities: local memory and storage (if available), multiple syslog servers and multiple Hillstone Security Audit (HSA) platforms
- Encrypted logging and log integrity with HSA scheduled batch log uploading
- Reliable logging using TCP option (RFC 3195)
- Detailed traffic logs: forwarded, violated sessions, local traffic, invalid packets
- Comprehensive event logs: system and administrative activity audits, routing & networking, VPN, user authentications, WiFi related events
- IP and service port name resolution option
- Brief traffic log format option
- Three predefined reports: Security, Flow and network reports
- User defined reporting
- Reports can be exported in PDF, Word and HTML via Email and FTP
Statistics and Monitoring
- Application, URL, threat events statistic and monitoring
- Real-time traffic statistic and analytics
- System information such as concurrent session, CPU, Memory and temperature
- iQOS traffic statistic and monitoring, link status monitoring
- Support traffic information collection and forwarding via Netflow (v9.0)
CloudView
- Cloud-based security monitoring
- 7/24 access from web or mobile application
- Device status, traffic and Threat monitoring
- Cloud-based log retention and reporting