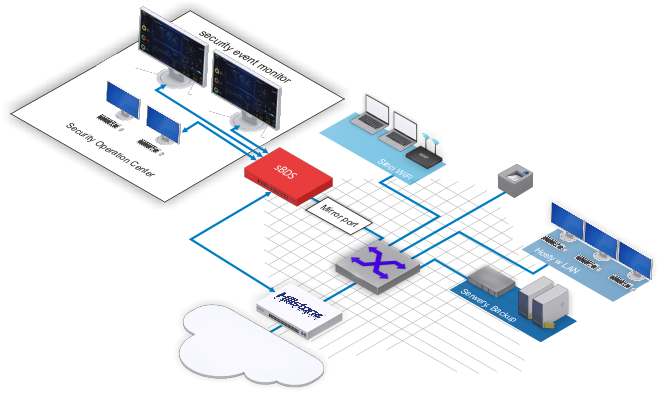
Platforma korelacji zagrożeń Hillstone analizuje szczegóły związków, każdego podejrzanego zdarzenia związanego z zagrożeniem, a także inne informacje kontekstowe w sieci, aby połączyć kropki i zapewnić dokładne i skuteczne wykrywanie złośliwego oprogramowania i ataków o wysokim poziomie ufności. System klasy NDR Hillstone sBDS to podstawa każdego wysoko bezpiecznego działy SOC. Platforma sBDS jest częścią całego ekosystemu bezpieczeństwa firmy Hillstone Networks.

Hillstone Seria I (ochrona infrastruktury typu NDR)
Hillstone NDR Server Breach Detection System (sBDS) przyjmuje wiele technologii wykrywania zagrożeń, które obejmują zarówno tradycyjną technologię opartą na sygnaturach, jak i inteligentne modelowanie danych na dużą skalę oraz modelowanie analityki behawioralnej użytkownika, co stanowi idealne rozwiązanie do wykrywania nieznanych lub 0-dniowych ataki z zagrożeniem, aby chronić cenne, krytyczne serwery i ich wrażliwe dane przed wyciekiem lub kradzieżą. Wraz z możliwościami głębokiej analizy zagrożeń i ich widoczności, Hillstone NDR zapewnia administratorom bezpieczeństwa skuteczne środki do wykrywania zdarzeń IOC (Wskaźników Kompromisu), przywracania łańcucha zabójstw ataków z wykorzystaniem zagrożeń oraz zapewnienia szerokiego wglądu w analizę i ograniczanie zagrożeń
Case Studies:
Pełna analiza forensic (kryminalistyczna)
Platforma sBDS firmy Hillstone przeprowadza szybkie ograniczanie incydentów i zagrożeń w połączeniu z urządzeniami Hillstone NGFW serii E,T,A, które są umieszczone na obwodzie chronionej sieci.
Kompletne zapobieganie cyber-atakom
Hillstone sBDS drąży i ujawnia więcej analiz zagrożeń i inteligencji na temat tych zdarzeń MKOl, rekonstruując łańcuch ataku na podstawie tych MKOl i korelując inne zdarzenia zagrożeń związane z tymi MKOl w spektrum czasu i przestrzeni.
Specyfikacja:
Modele Server Breach Detection System (sBDS)
Hillstone I-1850

Server Breach Detection System
Breach Detection Throughput – 1Gbps

New Sessions/s – 15 000

Maximum Concurrent Sessions – 750 000

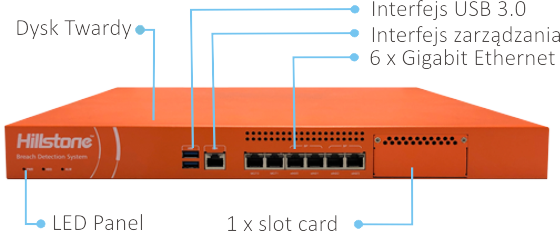
Dysk Twardy – 1T HDD

Hillstone I-2850

Server Breach Detection System
Breach Detection Throughput – 2Gbps

New Sessions/s – 30 000

Maximum Concurrent Sessions – 1 500 000

Dysk Twardy – 1T HDD

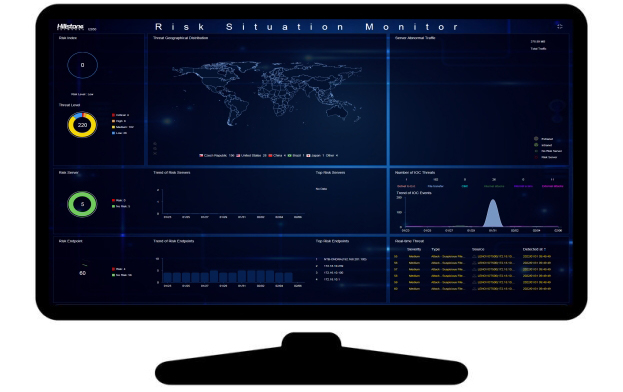
Monitorowanie zagrożeń w czasie rzeczywistym
Platforma sBDS firmy Hillstone Networks koncentruje się na ochronie krytycznych serwerów w intranecie. Jego wysoka dokładność obserwacyjna nadaje mu maksymalną skuteczność wykrywaniu nieznanych ataków wektorowych oraz 0-day. Dzięki ciągłej i pełnej obserwacji ruchu sieciowego (mirroring ruchu) sBDS jest w stanie wykryć nieprawidłowe działania sieciowe. Monitoruje serwery oraz w pełni obserwuje łączące się z nim hosty.

Hillstone I-1870

Server Breach Detection System
Breach Detection Throughput – 1Gbps

New Sessions/s – 32 000

Maximum Concurrent Sessions – 750 000

Dysk Twardy – 1T SSD


Hillstone I-2860

Server Breach Detection System
Breach Detection Throughput – 2Gbps

New Sessions/s – 75 000

Maximum Concurrent Sessions – 1 500 000

Dysk Twardy – 1T SSD


Hillstone I-3860

Server Breach Detection System
Breach Detection Throughput – 5Gbps

New Sessions/s – 210 000

Maximum Concurrent Sessions – 3 000 000

Dysk Twardy – 1T SSD


Hillstone I-5860

Server Breach Detection System
Breach Detection Throughput – 10Gbps

New Sessions/s – 500 000

Maximum Concurrent Sessions – 6 000 000

Dysk Twardy – 2T SSD

Hillstone I-3850

Server Breach Detection System
Breach Detection Throughput – 5Gbps

New Sessions/s – 40 000

Maximum Concurrent Sessions – 3 000 000

Dysk Twardy – 1T HDD

Hillstone I-5850

Server Breach Detection System
Breach Detection Throughput – 10Gbps

New Sessions/s – 160 000

Maximum Concurrent Sessions – 6 000 000

Dysk Twardy – 1T HDD

Systemy ochrony i usługi
Cloud-Sandbox
- Upload malicious files to cloud sandbox for analysis
- Support protocols including HTTP/HTTPS, POP3, IMAP, SMTP and FTP
- Support file types including PE,ZIP, RAR, Office, PDF, APK, JAR and SWF
- File transfer direction and file size control
- Provide complete behavior analysis report for malicious files
- Global threat intelligence sharing, real-time threat blocking
- Support detection only mode without uploading files
Threat Correlation Analytics
- Correlation among unknown threats, abnormal behavior and application behavior to discover potential threat or attacks
- Multi-dimension correlation rules, automatic daily update from the cloud
Advanced Threat Detection
- Behavior-based advanced malware detection
- Detection of more than 2000 known and unknown malware families including Virus, Worm, Trojan, Overflow etc.
- Real-time, online, malware behavior model database update
Abnormal Behavior Detect
- Behavior modeling based on L3-L7 baseline traffic to reveal anomalous network behavior, such as HTTP scanning, Spider, SPAM, SSH/FTP weak password
- Detection of DDoS including Flood, Sockstress, zip of death, reflect, DNS query, SSL DDos and application DDoS
Supports inspection of encrypted tunneling traffic for unknown applications - Real-time, online, abnormal behavior model database update
Deception Threat Detection
- Local deception engine with regular deception models update
- Simulate to Web, Doc or Database Servers, support protocols including FTP, HTTP, MYSQL, SSH and TELNET
Intrusion Detection
- 8,000+ signatures, protocol anomaly detection and rate-based detection
- Custom signatures, manual, automatic push or pull signature updates, integrated threat encyclopedia
- Over 20 types of protocols anomaly detection, including HTTP, SMTP, IMAP, POP3, VOIP, NETBIOS, etc.
- Support for buffer overflow, SQL injection and cross-site scripting attack detection
Virus Scan
- 4 million virus signature database
- Online real-time updates
- Compressed file scans
Anti-Spam
- Real-time Spam Classification and Prevention
- Confirmed Spam, Suspected Spam, Bulk Spam, Valid Bulk
- Protection Regardless of the language, format, or content of the message
- Support both SMTP and POP3 email protocols
- Whitelists to allow emails from trusted domain/email addresses
Cloud-Sandbox
- Upload malicious files to cloud sandbox for analysis
- Support protocols including HTTP, SMTP, POP3, IMAP4 and FTP
- Support file types including PE, APK, JAR, MS-Office, PDF, SWF, RAR, ZIP
- Provide complete behavior analysis report for malicious files
- Global threat intelligence sharing, real-time threat blocking
- Multiple static detection engines quickly filter normal files and known threats
- Unknown threat visualization based on logs, reports, monitoring information, file behavior reports
Botnet C&C Prevention
- Discover intranet botnet host by monitoring C&C connections and block further advanced threats such as botnet and ransomware
- Regularly update the botnet server addresses
- prevention for C&C IP and domain
- Support TCP, HTTP, and DNS traffic detection
- IP and domain whitelists
Attack Detection
- Abnormal protocol attack detection
- DoS/DDoS detection, including SYN Flood, DNS Query Flood etc.
- ARP attack detection
Application identification
- Over 3,000 applications that can be filtered by name, category, subcategory, technology and risk
- Each application contains a description, risk factors, dependencies, typical ports used, and URLs for additional reference
- Actions: block, reset session, monitor, traffic shaping
- Identify and control applications in the cloud
- Provide multi-dimensional monitoring and statistics for applications running in the cloud, including risk category and characteristics
Threat Mitigation
- Admin actions to change threat events status, open, false positive, fixed, ignore, confirmed
- Threat events whitelist, including threat name, source/destination IP, hit count etc.
- Conjunction with Hillstone firewall platforms to block threat
Monitoring
- Dynamic, real-time dashboard status and drill-in monitoring widgets
- Overview of internal network risk status, including critical assets risk status, host risk status, threat severity and type, external attack geo-locations, etc.
- Visual details of threat status for critical assets and other risky host, including risk level, risk certainty, attack geo-location, kill chain mapping and other statistical information
- Visual details of network threat events, including name, type, threat severity and certainty, threat analysis, knowledge base and history
- Send alarm via Email and Trap
- Cloud-based threat intelligence push service
Administration
- Management access: HTTP/HTTPS, SSH, telnet, console
- Central management: Hillstone Security Manager (HSM), web service APIs
- System integration: SNMP, syslog, alliance partnerships
- Rapid deployment: USB auto-install, local and remote script execution
- Dynamic real-time dashboard status and drill-in monitoring widgets
- Language support: English
Logs & reporting
- Logging facilities: local memory and storage (if available), multiple syslog servers and multiple Hillstone Security Audit (HSA) platforms
- Encrypted logging and log integrity with HSA scheduled batch log uploading
- Reliable logging using TCP option (RFC 3195)
- Detailed traffic logs: forwarded, violated sessions, local traffic, invalid packets
- Comprehensive event logs: system and administrative activity audits, routing & networking, VPN, user authentications, WiFi related events
- IP and service port name resolution option
- Brief traffic log format option
- Three predefined reports: Security, Flow and network reports
- User defined reporting
- Reports can be exported in PDF, Word and HTML via Email and FTP
CloudView
- Cloud-Bases security management
- 7/24 access from Web or mobile application
- Device, traffic and threat monitoring
SBDS pełna widoczność ataków sieciowych oraz automatyzacja odpowiedzi na zagrożenia